Which two statements characterize wireless network security choose two – Which two statements characterize wireless network security? Choose two. This question delves into the critical aspects of securing wireless networks, exploring the fundamental principles and best practices that safeguard data and privacy in an increasingly connected world. Join us as we unravel the complexities of wireless network security, examining the authentication methods, encryption protocols, access control mechanisms, network monitoring techniques, and industry standards that shape the landscape of wireless network protection.
In this comprehensive guide, we will delve into the intricacies of wireless network security, empowering you with the knowledge and insights necessary to protect your networks from potential threats and vulnerabilities. As we navigate through the key concepts and strategies, you will gain a deeper understanding of the measures required to ensure the confidentiality, integrity, and availability of your wireless networks.
Wireless Network Security
Wireless networks offer convenience and flexibility, but they also introduce unique security challenges. To protect wireless networks from unauthorized access and data breaches, it is crucial to implement robust security measures.
Authentication Methods: Which Two Statements Characterize Wireless Network Security Choose Two
Authentication is the process of verifying the identity of a user or device attempting to access a wireless network. There are two primary authentication methods used in wireless networks:
Open Authentication
- No credentials required to connect.
- Easy to implement, but provides minimal security.
Shared Key Authentication
- Requires a shared secret key to connect.
- More secure than open authentication, but vulnerable to key compromise.
| Authentication Method | Security Level | Ease of Implementation | Cost ||—|—|—|—|| Open Authentication | Low | High | Low || Shared Key Authentication | Medium | Medium | Low |
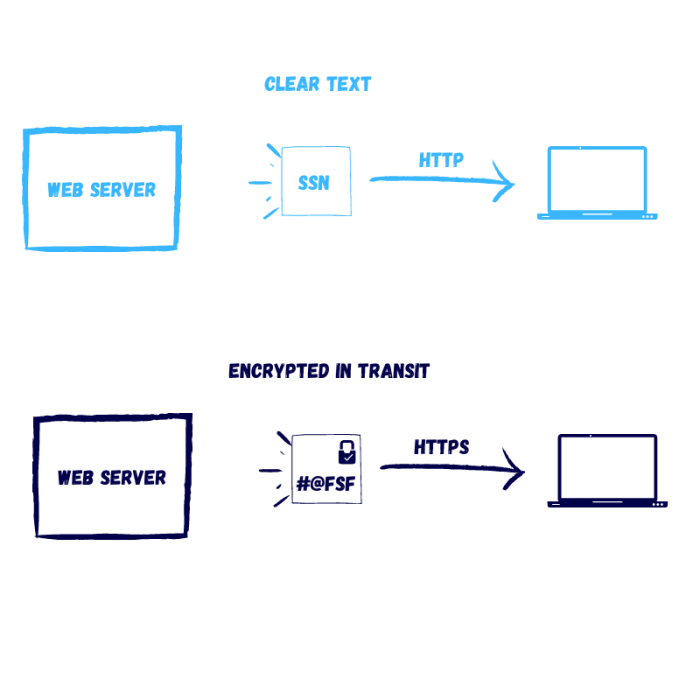
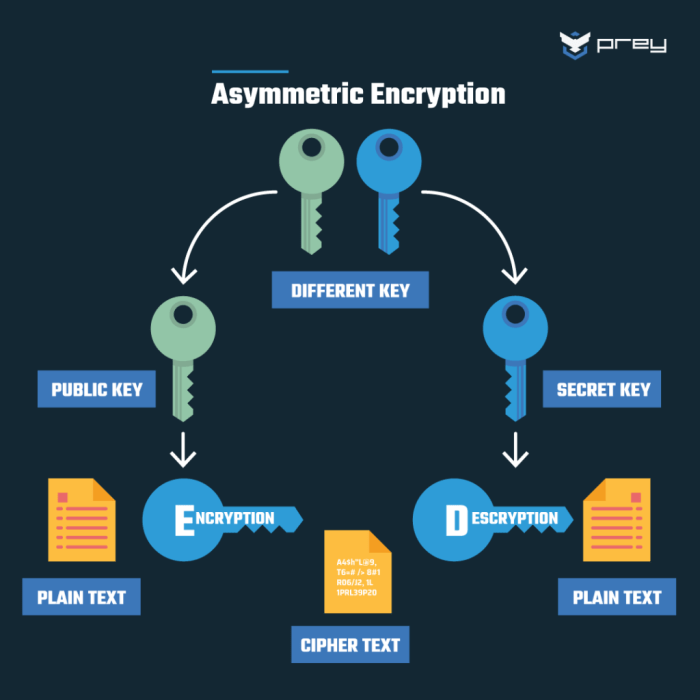
Encryption Protocols
Encryption is the process of converting plaintext data into ciphertext, making it unreadable to unauthorized parties. There are two widely used encryption protocols in wireless networks:
Wired Equivalent Privacy (WEP)
- Legacy encryption protocol with weak security.
- Easily cracked using readily available tools.
Wi-Fi Protected Access (WPA/WPA2), Which two statements characterize wireless network security choose two
- More robust encryption protocols with stronger security.
- WPA2 is the current recommended standard for wireless network encryption.
| Encryption Protocol | Encryption Strength | Speed | Compatibility ||—|—|—|—|| WEP | Weak | Fast | Legacy devices only || WPA | Medium | Moderate | Most modern devices || WPA2 | Strong | Slowest | Modern devices |
Access Control Mechanisms
Access control mechanisms restrict access to wireless networks based on specific criteria:
Media Access Control (MAC) Filtering
- Blocks devices based on their MAC addresses.
- Easy to implement, but MAC addresses can be spoofed.
802.1X Authentication
- Uses an external authentication server to verify user credentials.
- Provides strong security, but requires additional infrastructure.
Network Monitoring and Intrusion Detection
Network monitoring and intrusion detection techniques help detect and prevent security threats in wireless networks:
Intrusion Detection Systems (IDS)
- Monitor network traffic for suspicious activity.
- Can detect and alert on security breaches.
Network Access Control (NAC)
- Enforces network access policies and restricts access to unauthorized devices.
- Helps prevent malware and other security threats.
| Technique | Effectiveness | Cost | Complexity ||—|—|—|—|| IDS | High | Moderate | Complex || NAC | Medium | High | Moderate |
Compliance and Best Practices
Adhering to industry standards and best practices is crucial for wireless network security:
IEEE 802.11i Standard
- Defines security requirements for wireless networks.
- Provides a framework for implementing robust security measures.
Use Strong Passwords and Encryption
- Choose complex passwords and encryption keys.
- Regularly change passwords and encryption keys to prevent unauthorized access.
Following industry standards and best practices ensures that wireless networks are protected against the latest security threats, reducing the risk of data breaches and unauthorized access.
Question & Answer Hub
What are the two most common authentication methods used in wireless networks?
The two most common authentication methods used in wireless networks are Pre-Shared Key (PSK) and Extensible Authentication Protocol (EAP).
What are the two most widely used encryption protocols in wireless networks?
The two most widely used encryption protocols in wireless networks are Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA).
What are the two main access control mechanisms employed in wireless networks?
The two main access control mechanisms employed in wireless networks are Media Access Control (MAC) filtering and role-based access control (RBAC).
What are two essential network monitoring and intrusion detection techniques used in wireless networks?
Two essential network monitoring and intrusion detection techniques used in wireless networks are intrusion detection systems (IDS) and intrusion prevention systems (IPS).
What are two industry standards or best practices related to wireless network security?
Two industry standards or best practices related to wireless network security are the IEEE 802.11i standard and the National Institute of Standards and Technology (NIST) Cybersecurity Framework.